We have another very sneaky scam that’s hot off the presses. This time, it’s personal.
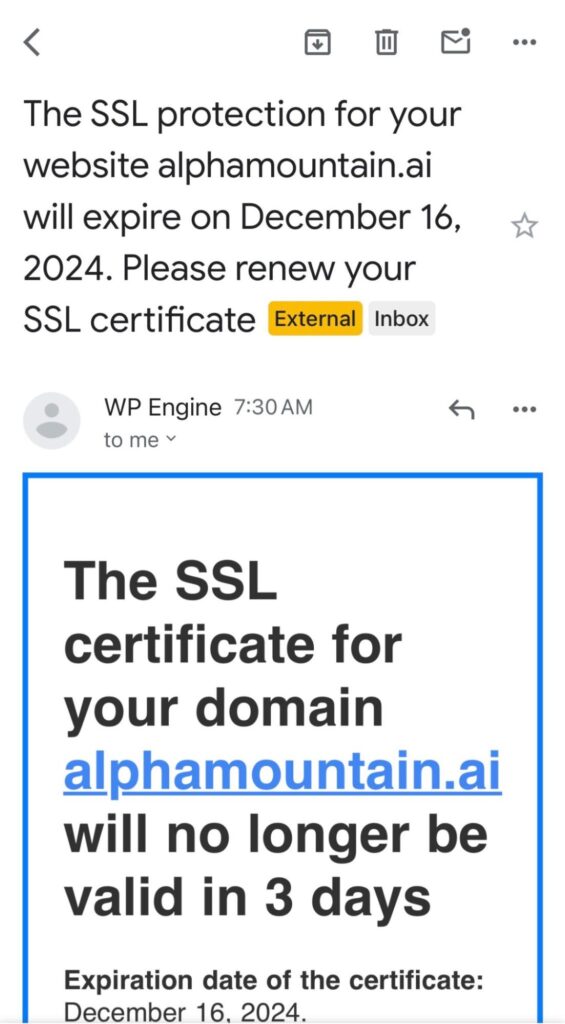
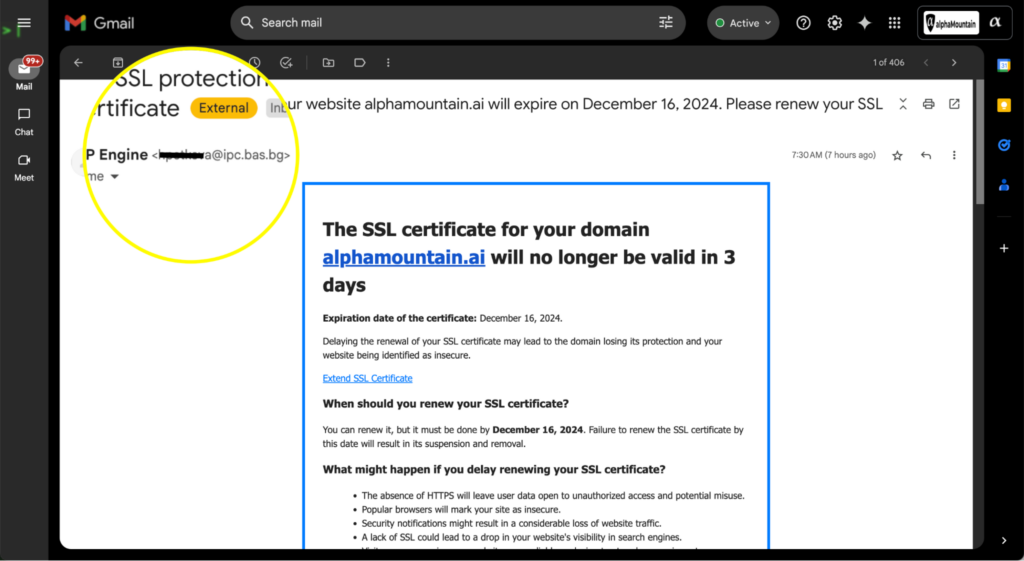
Like millions of other websites, our website is hosted on a platform called WP Engine. Our site is managed by our marketing team, and this morning they received an email from “WP Engine” informing them that our site’s SSL certificate would expire in three days.
That’s great customer service.
Or is it?
Let’s dig in.
Extensive Email Personalization & copy
The email notification came in at 7:30AM on the dot. That’s exactly what you’d expect from a valid transactional email, for it to arrive near or on the hour or half hour.
The ‘from’ name is “WP Engine” (our hosting provider) and the copy in the email body is all perfect English.
The first line mentions and links to our real corporate domain (alphamountain.ai) making it highly relevant and personalized.
The subject and call to action are both clear.
These are all signs of a legitimate email.
That said, there are a few things missing from the email that you might expect to see including a logo and a footer, but nothing glaring.
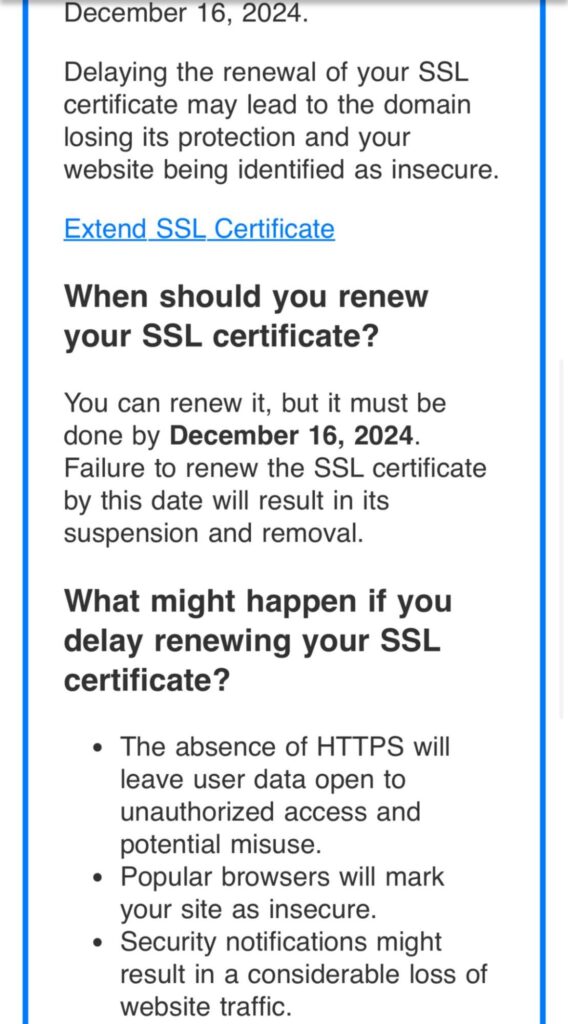
So far, no real red flags, so let’s click on the call to action: “Extend SSL Certificate”
Well-Designed Landing Page
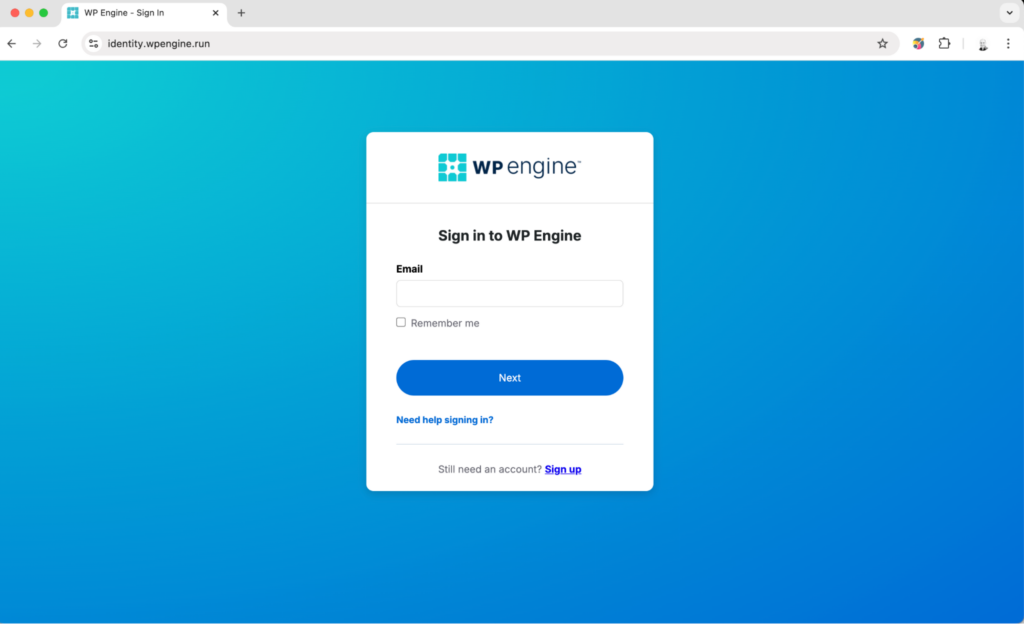
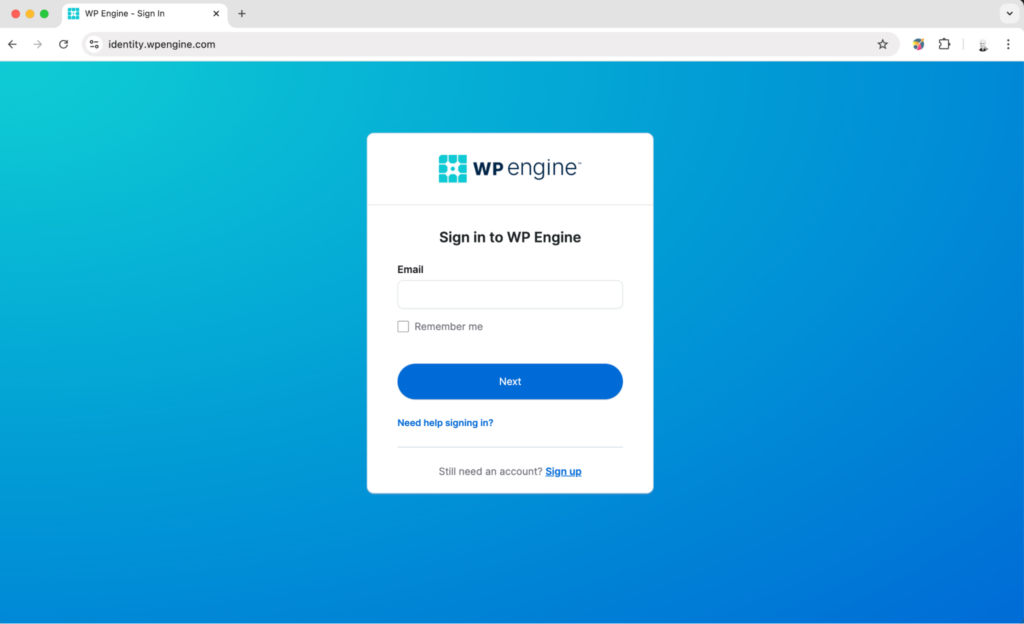
When we click on the link email, this is what we see.
Whatever the initial email was lacking in terms of branding, the landing page makes up for it.
It is well branded and includes the WP Engine logo and links to their actual resources on their corporate domain.
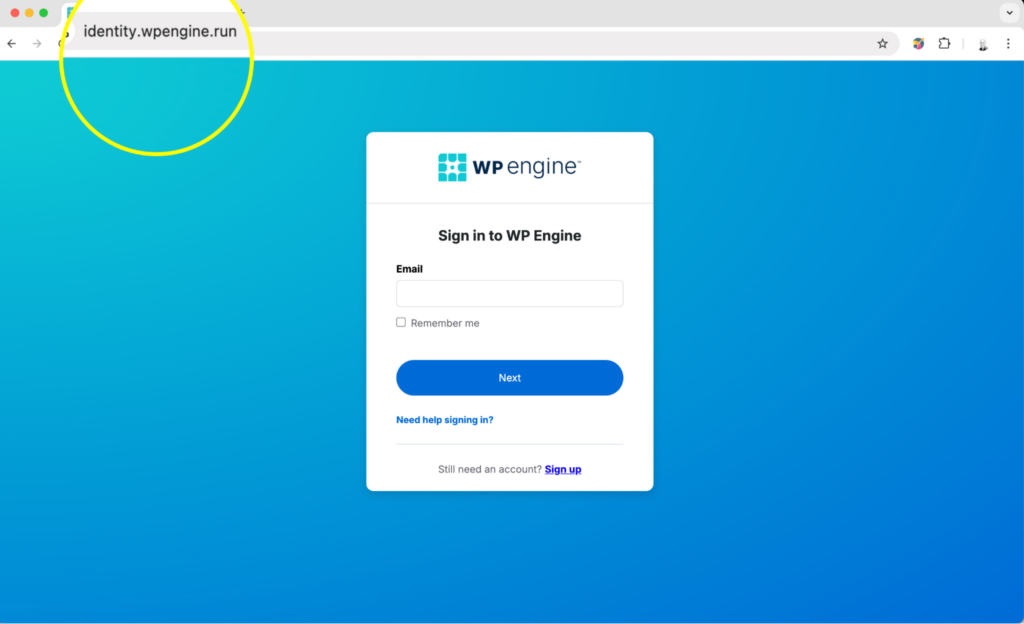
Speaking of domains, let’s look at the landing page URL: identity.wpengine.run If the initial email was devoid of any serious red flags, this landing page is starting to raise them.
A quick visit to the WP engine website reveals that the authentic login page is actually identity.wpengine.com – this suspicious site is remarkably close.
The .run top level domain was no doubt chosen for its tech relevance, cost and ability to pass the security sniff test that other generic TLDs like .top, .xyz or .fun seem to fail by default.
We are now 100% sure this is a phishing site based on the URL alone, but just for comparison’s sake, here is the authentic WP Engine site.
They are, for all intents and purposes, identical.
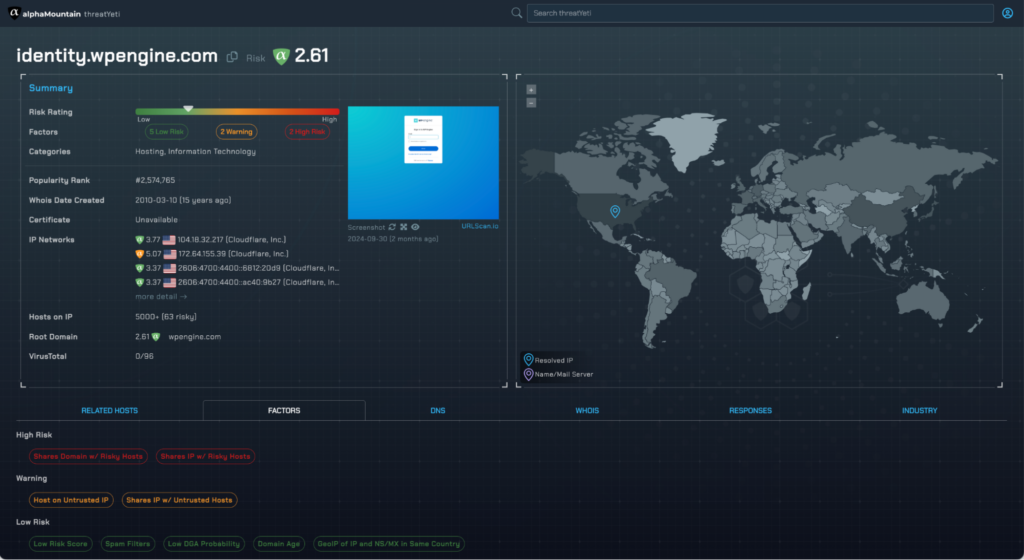
Now, let’s compare the two sites in threatYeti.com, alphaMountain’s domain and IP investigation solution.
The authentic site:
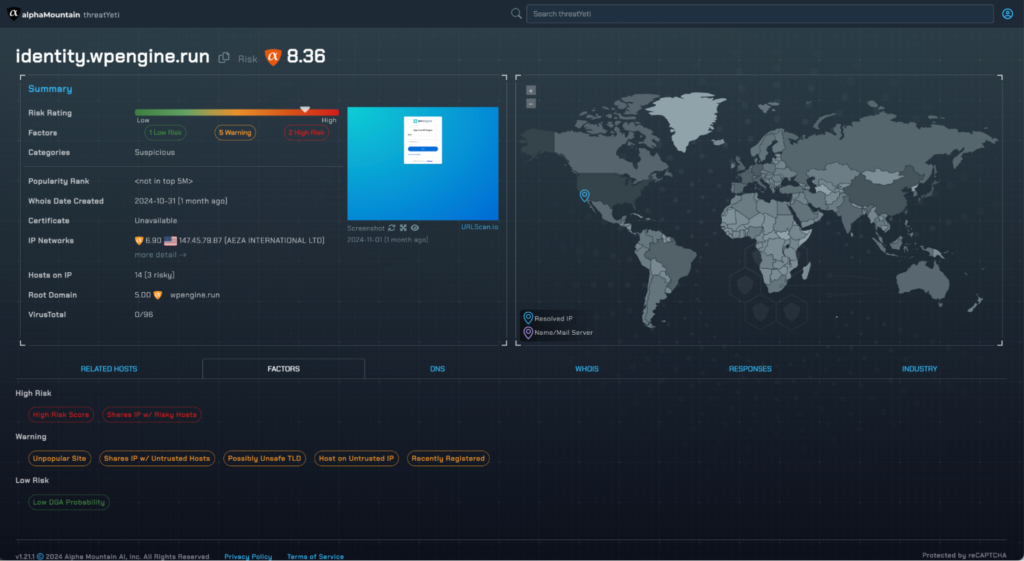
Now, the suspicious site:
With threatYeti’s intuitive interface, right away we can see the category label of ‘Suspicious’, and threat factors that stand out, including the site sitting on an untrusted IP, and a recently-registered domain on a possibly-untrusted TLD.
Also, take a look at that resolved IP address. It’s sitting at a 6.90 which is just under our threshold of 7.0 for high risk.
If you haven’t already, you should check out our recent research on risky ASNs and the data that powered that report shows that this ASN has 46% of its IP addresses falling above 7.0, with an average risk score of 8.719.
| asn | count | avg | risky_count | risky_avg | % risky | as_name |
| AS210644 | 46047 | 6.524 | 21,238 | 8.719 | 46% | AEZA INTERNATIONAL LTD |
When threatYeti indicates “Host on Untrusted IP”, this is what it means.
Advanced Evasion Techniques
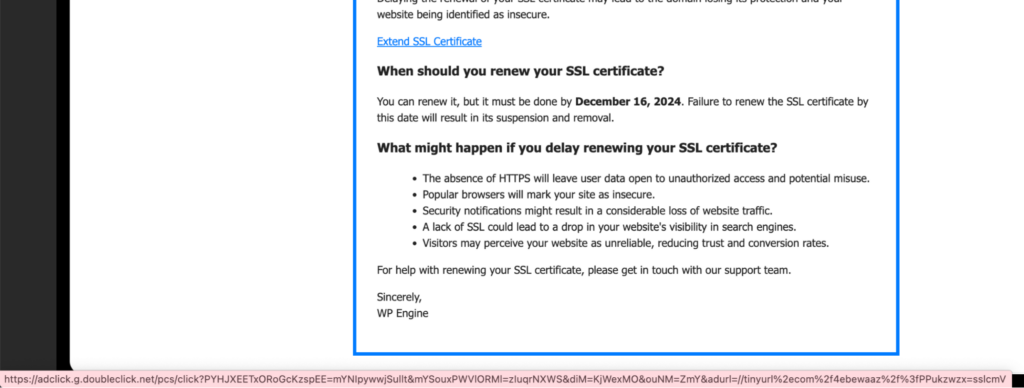
If we go back to the original email, there are two very sneaky tactics that the threat actors used to evade email security solutions.
The first sneaky tactic is when we hover over the call to action, “Extend SSL Certificate”, we see that the link actually points to the doubleclick.net domain.
You might recognize this domain as the tracking domain to which all Google advertising campaigns link back.
The use of this trusted link in the email call to action enables it to evade threat detection.
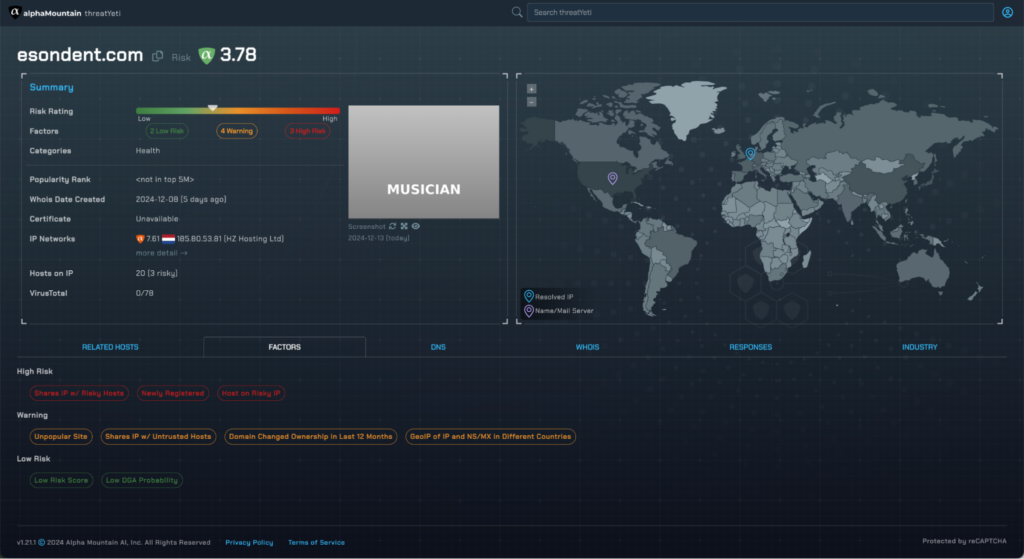
Sneaky tactic number two is that, in this case, the link forwards temporarily to a relatively benign domain esondent.com. As you see here in the screenshot captured on threatYeti.com, that domain is low risk, with a screenshot indicating that it’s a live host at the time of capture.
The threat actors actually engineered a cunning delay into that domain’s redirection so that any detonation of the original URL from the email would be seen resolving to a benign domain–temporarily.
It’s worth noting that even this temporary landing page is on an even riskier IP than the final domain with this layover destination coming in at 7.61 according to threatYeti.com
After some time, that URL itself eventually resolves to the suspicious wpengine.run URL detailed above.
Presumably, this redirection was programmed to happen a short while after the campaign was delivered to email inboxes and after any security solution would have scanned and/or detonated the doubleclick.net URL.
This delay would have enabled the emails to successfully evade phishing detection while also landing recipients on the final, malicious landing page.
Full Disclosure
Truth be told, our marketing team received this email and immediately forwarded it to the person in charge of SSL because, as a marketer, there isn’t much scarier than the thought of your website going dark. That exchange went as follows:
Marketing Person: I’m sure you got this as well but this is kind of urgent for only a 3 day warning. 😅
SSL Person: Not sure where they got their info. Our cert actually expires on Jan. 31. <<screenshot of certificate viewer>>
Marketing Person: OMG it’s phishing.
This email totally passed the vibe test from our early morning, pre-coffee cursory glance. It didn’t help that the email was originally viewed on a mobile device where the sender address wasn’t visible by default.
Had it been viewed on a desktop email client, it would have been much more obvious at first glance that this was indeed a suspicious email since the sender email address is completely unrelated to WP Engine brand or domain.
Luckily, we were not compromised by this campaign, but we worry that others might be, so we put together this post to help spread the word.
If you’re ever in doubt about a link or URL such as those in this (likely phishing) campaign, use threatYeti.com to get a free and full security report on it.