If you live in the United States, you might have recently received an SMS message indicating that you have a payment due for “The Toll Roads.”
While the concept of toll roads is a familiar one to most Americans, The Toll Roads is actually a formal operating entity owned by the State of California, specifically in Orange County.
If you have driven recently in southern California, receiving this message might actually cause some anxiety. Fines for late or unpaid tolls can quickly reach triple digits.
On the other hand, if you have never heard of The Toll Roads or have not driven recently in southern California, you would likely quickly flag this unexpected SMS message for what it is: a scam.
Let’s understand what’s behind this latest scam by using alphaMountain’s URL analysis solution, threatYeti, to take a look at one of the URLs these campaigns are pointing to.
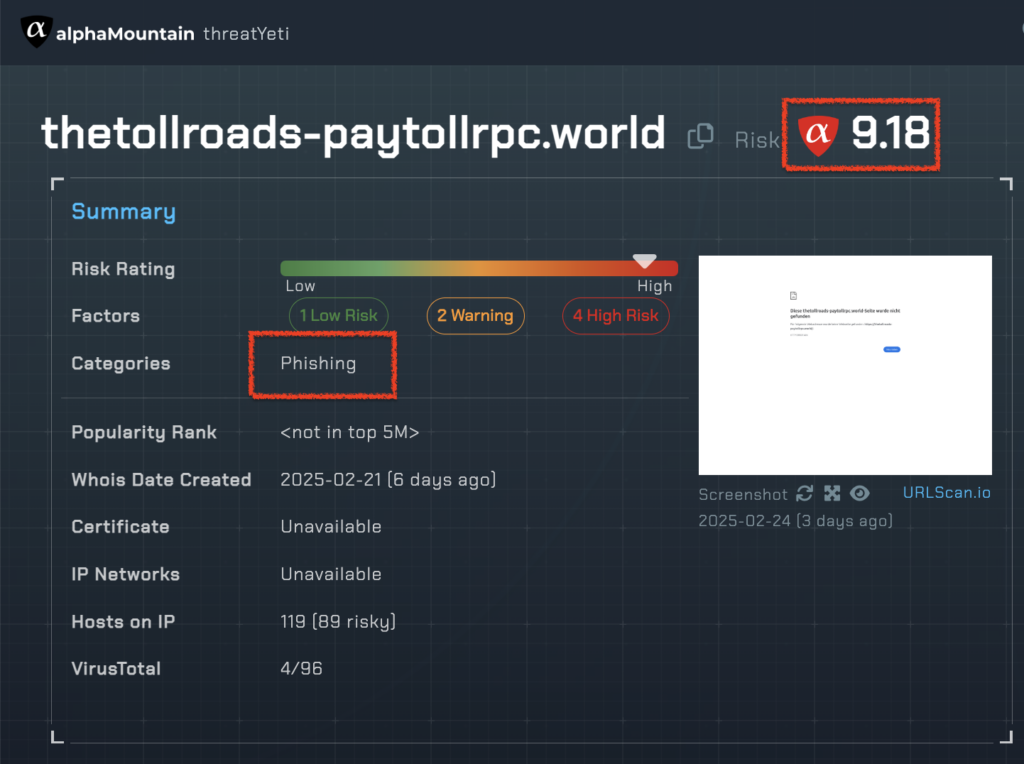
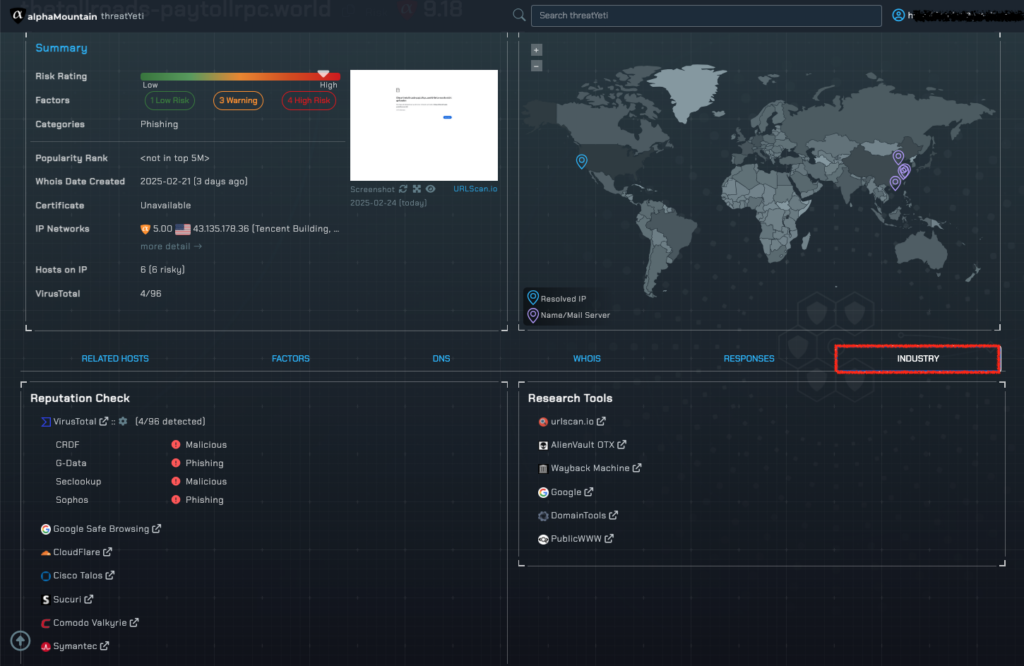
Threat Score & URL Category
When we input the URL from a similar SMS campaign, thetollroads-paytollrpc.world, threatYeti instantly returns a high risk score of 9.18.
For reference, threatYeti’s URL threat ratings range from 1.00 (very safe) to 10.0 (extremely risky).
This is a very risky site.
We can also see the URL classification for the site as “Phishing”.
While the site is now offline just three days after launch, had you reacted with the urgency the campaign requested, you would likely have found a payment form that would have simply stolen funds from your account.
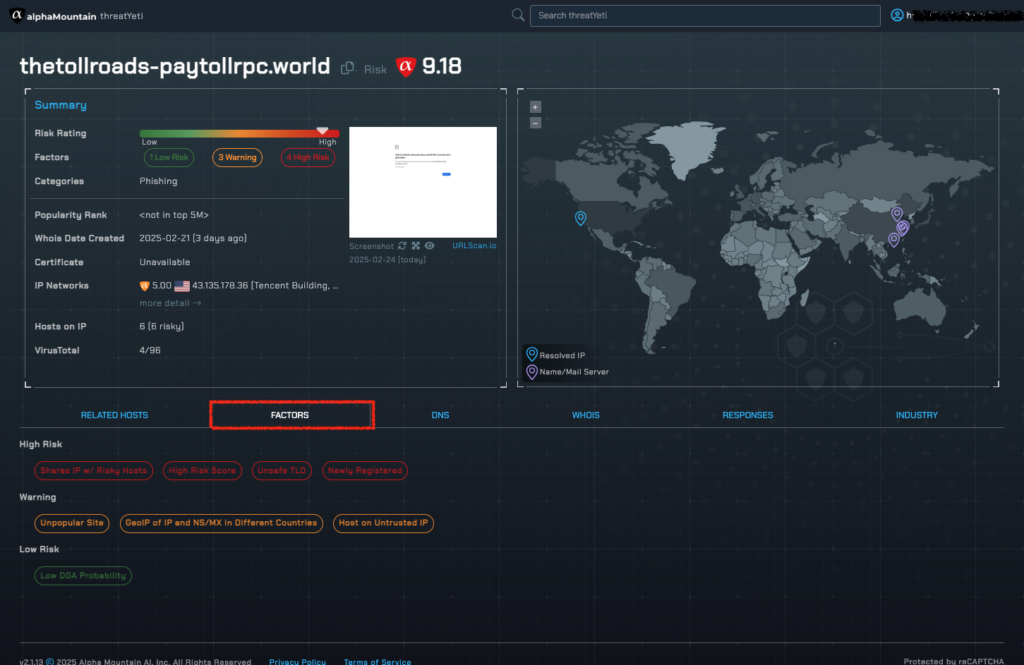
Threat Factors
URL threat ratings and content classification are used to create policies for network security products such as secure web gateways (SWG), endpoint detection and response (EDR) and secure browsers.
However, in the course of an investigation or incident response, threat ratings and URL classification might not provide the whole picture as to “why” a domain or link is considered either risky or safe.
alphaMountain’s exclusive threat factors show you exactly why a domain threat verdict is what it is and what factors contribute to its posture.
In this case, we see several high risk factors including that the URL sits on a top-level domain that is known to frequently be associated with risky sites (.world).
We also see that the site is newly registered and that it’s served from an IP address with other known risky hosts.
Other, medium-risk factors include the locations of the IP address, name and mail servers being in different countries and the fact that the site is unpopular (not in the top five million sites).
Popular sites are less likely to be risky.
In this case the IP address is geolocated to a server in Santa Clara, CA while the nameservers are in various locations in mainland China.
threatYeti shows us how this discrepancy between DNS records contributes to the URL’s high risk score.
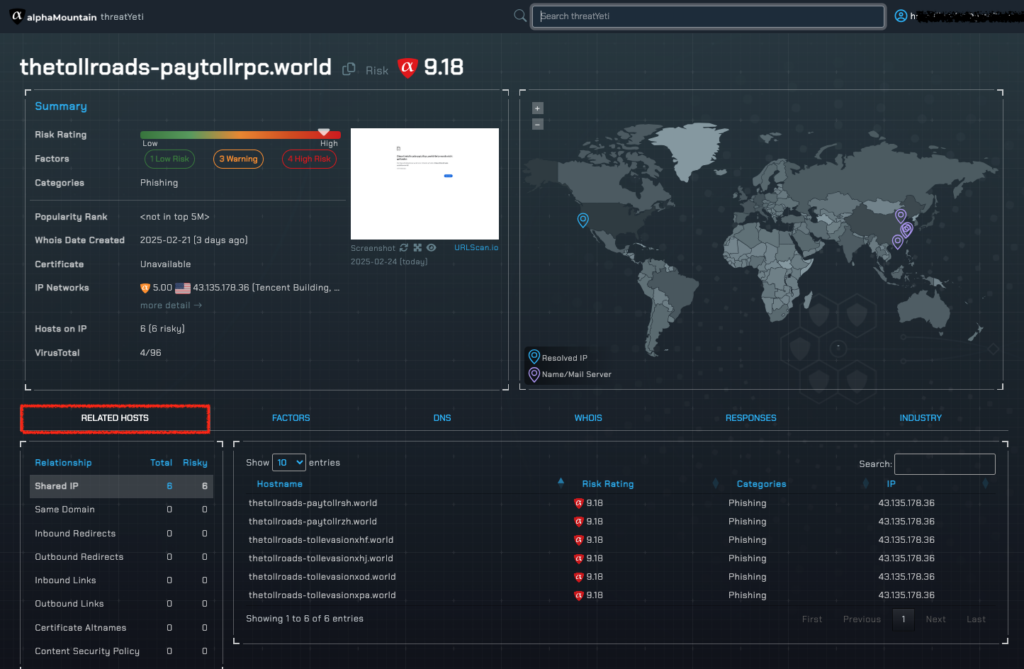
Related Hosts
threatYeti also shows us what other hosts might be related to the domain, thetollroads-paytollrpc.world.
If we click on the the Related Hosts tab, we see that there are six domains hosted on this same IP address and all of them are risky.
A closer look at the domains indicates that they are all three-letter variations of the strings …paytoll and …tollevasion, and all carry identical risk scores.
The threat actor(s) behind this phishing campaign were deliberate in its setup, using not only The Toll Roads brand, but also real-sounding context and human-readable calls to action. This effort helps to improve its effectiveness.
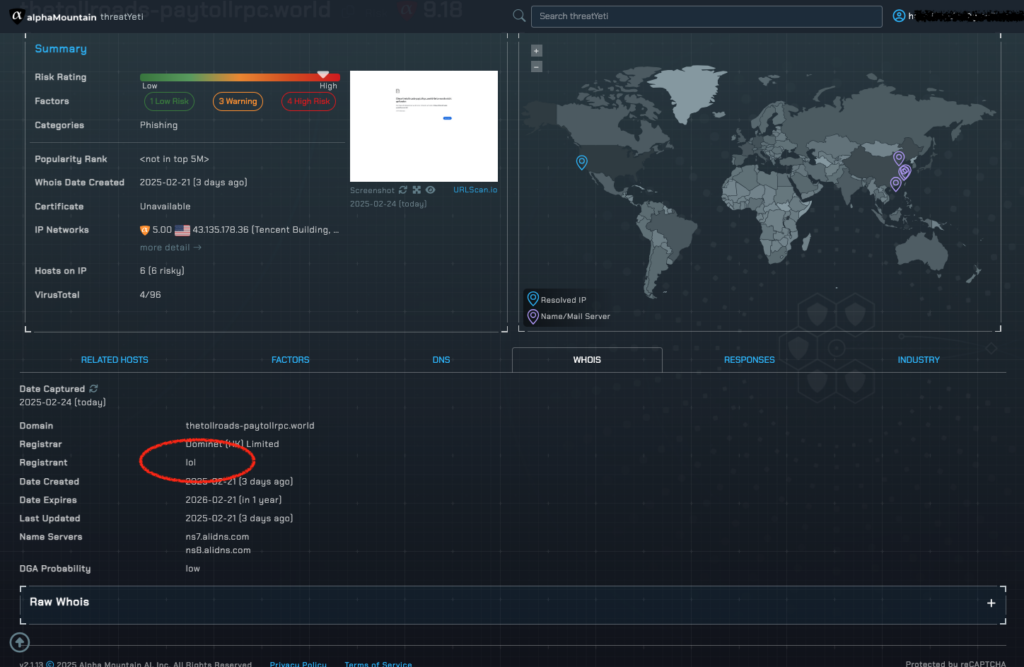
WHOIS
WHOIS records provide a wealth of information about a domain, including when it was first registered. When public, WHOIS information can also tell us what organization or individual owns the domain. In today’s environment, the reality is that most of this information is usually redacted or kept private at the request of the registrant.
However, the domain registrant for this campaign appears to have had some fun with the registration information. Whereas most individuals would simply opt to have all their information kept private, this person instead entered ‘lol’ in the registrant field.
While not at all helpful in identifying the actual threat actor behind this campaign, this flippant entry is ultimately supportive of the nefarious nature that the threat verdicts in threatYeti portray.
Industry Links & Research
Finally, when using threatYeti for analysis, investigation or incident response, you can call on third-party industry resources for additional context or validation.
By navigating to the Industry tab, you can easily look up the domain in question with one-click access to a number of additional services including Cisco Talos, Symantec, URLscan, Wayback Machine and more.
Additionally, with threatYeti Pro, you can integrate a free VirusTotal API key to display their crowdsourced threat verdicts directly in threatYeti.
Try threatYeti Free
Level up your threat investigations and URL analysis with a free threatYeti community account. Register with just an email address and you’ll unlock 25 queries per day to empower and enrich your investigations with HD Intelligence from alphaMountain.