It’s been an interesting several months for consumers. On one hand, inflation has eased and the federal reserve has reduced interest rates. On the other hand, prices remain elevated and credit card debt is at an all time high.
With this unprecedented demand for consumer credit, it should come as no surprise that threat actors have continued to prey upon the seemingly incessant flow of consumers looking to increase their purchasing power.
We recently came across a phishing campaign that took a novel approach to getting the personal information of American Express card holders.
Let’s dig in.
Landing Page
The landing page for the campaign sits on the URL platinumcardsapprovalform[.]in.
(Note: we came across the URL in our research. Delivery mechanisms in the wild are unknown but presumably are one or more of email, SMS or social media.)
The semantic structure of the domain, “platinum cards approval form” is aligned with and relevant to the content on the page itself.
This is a good practice from the threat actor so as to evade detection by legacy URL threat detection solutions.
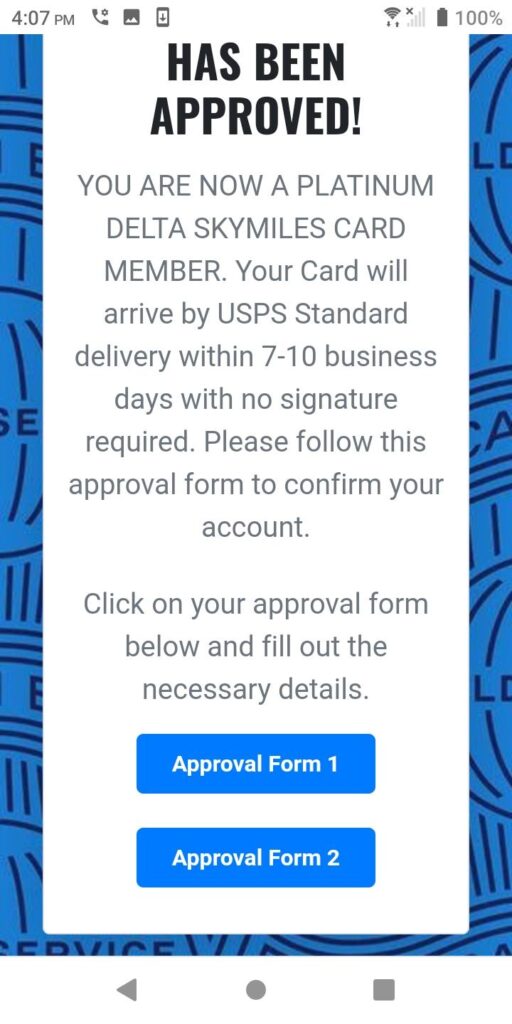
The American Express-branded and well-designed landing page notes that the recipient is now a “PLATINUM DELTA SKYMILES CARD MEMBER” and states that you must access a linked approval form to confirm your account.
So far, this is a fairly unremarkable experience.
Call(s) to Action
It’s not until you scroll down that the proverbial red flags start to appear. The most obvious is the presence of not one, but two calls to action. One would be expected, but two is just strange.
Moreover, the button labels, ‘Approval Form 1’ and ‘Approval Form 2’, do not exactly come across as professional.
So, where do the button links go?
The link to “Approval Form 1” takes you to:
platinumcardsapprovalform[.]in/Approval Form 1.apk
The link to “Approval Form 2” is broken and goes nowhere.
As you may be aware, .apk is the file extension for Android applications.
If the presence of two buttons was strange, this is downright suspicious.
At this point, if the thought of installing an Android application from this landing page doesn’t send shivers down your spine, perhaps you are an octopus.
The red flags are now flailing wildly against a cloudless sky.
The Malicious Application
Clicking on the first link on an Android phone gives you a prompt to download the “Your Approval Form” app.
On most phones, you would have to change the default Android settings to allow downloads from unknown sources, however, in the Android user base this is not all that rare an action.
Once installed, you get the “Your Approval Form” app complete with the American Express logo.
Had you not just downloaded it from a suspicious landing page, this app might actually look reasonably legitimate.
But wait, there’s more…
It’s not uncommon for new applications to ask for permissions to conduct certain functions, but buckle up for these…
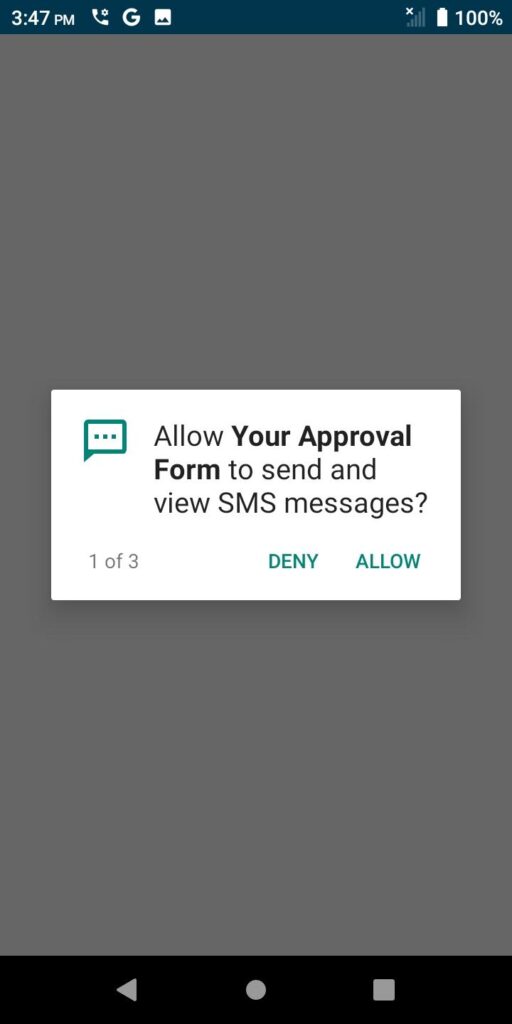
First, the app asks to be able to send and view SMS messages.
It’s worth pausing here to remember that you were supposed to be filling out a FORM (sorry for shouting, but c’mon) and now you have an application on your phone asking you to allow it to send and view SMS messages.
Say what?
This is unexpected.
But wait, there’s more.
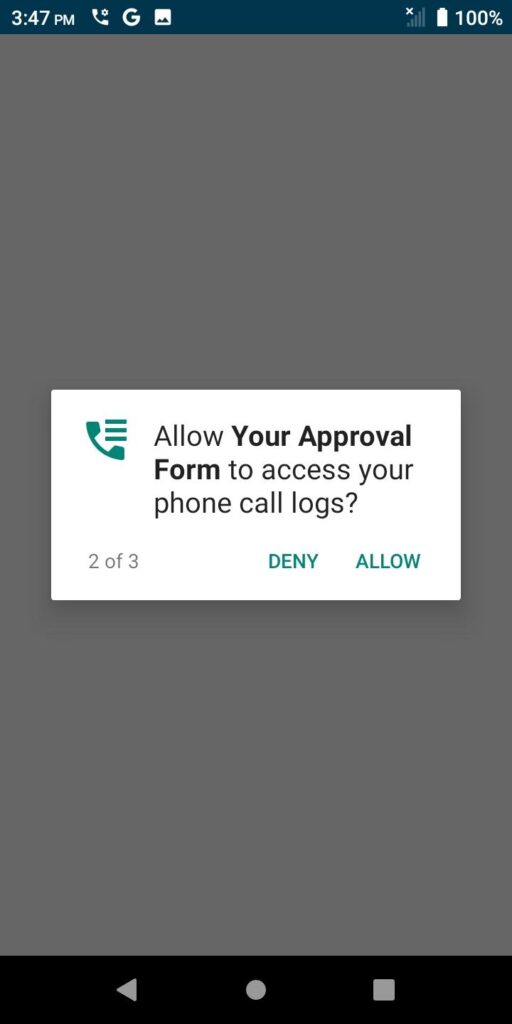
The app wants access to your call logs, too.
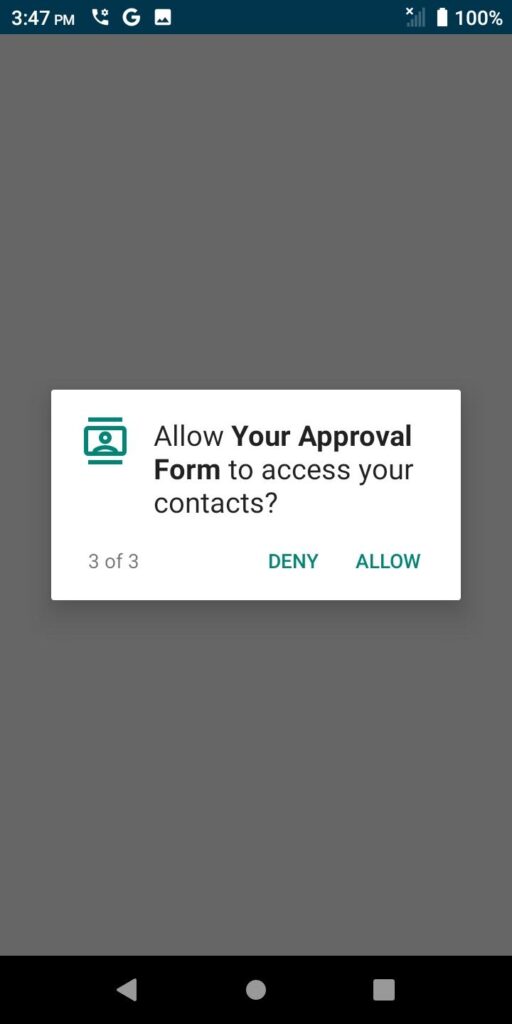
It also wants your contacts.
The seriousness of this malicious campaign is now coming into focus, but here comes the coup de grâce…
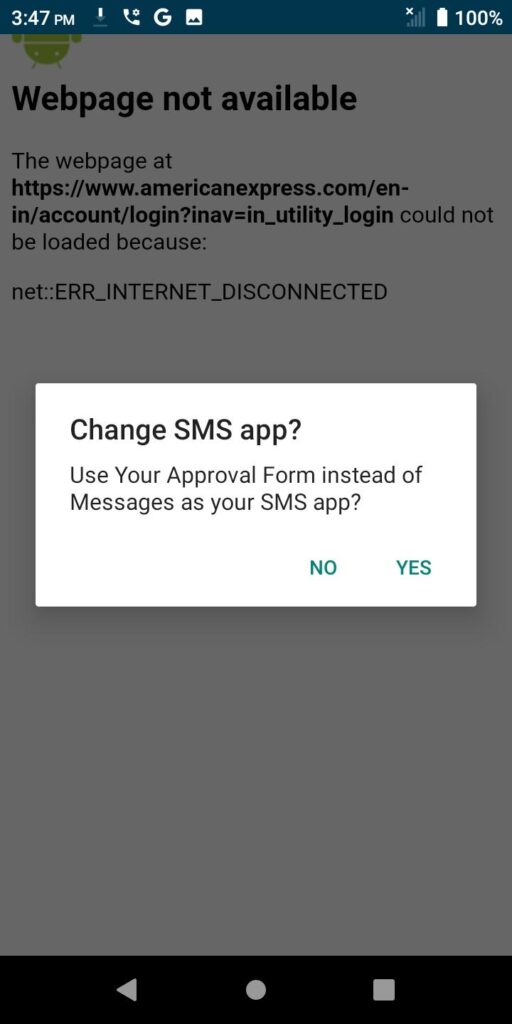
Finally, the app asks to become the default app for SMS instead of the ubiquitous “Messages” app native to all Android devices.
If you were to tap “Yes” to all of these requests, the application would be able to access all of your contacts, SMS messages and call logs. That seems like a bit much, doesn’t it?
Remember, you haven’t even seen the application at this point and it was supposed to be a form.
This is not good.
The Hack
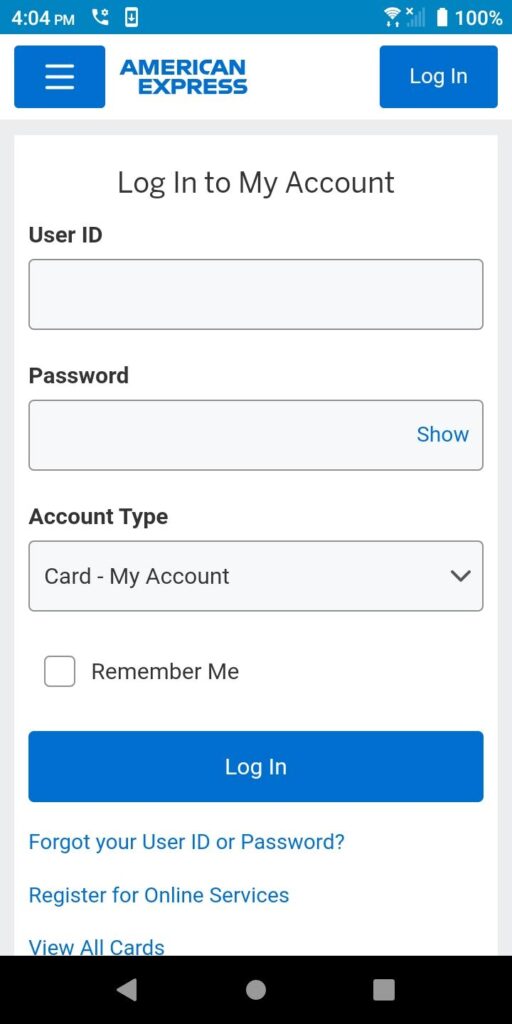
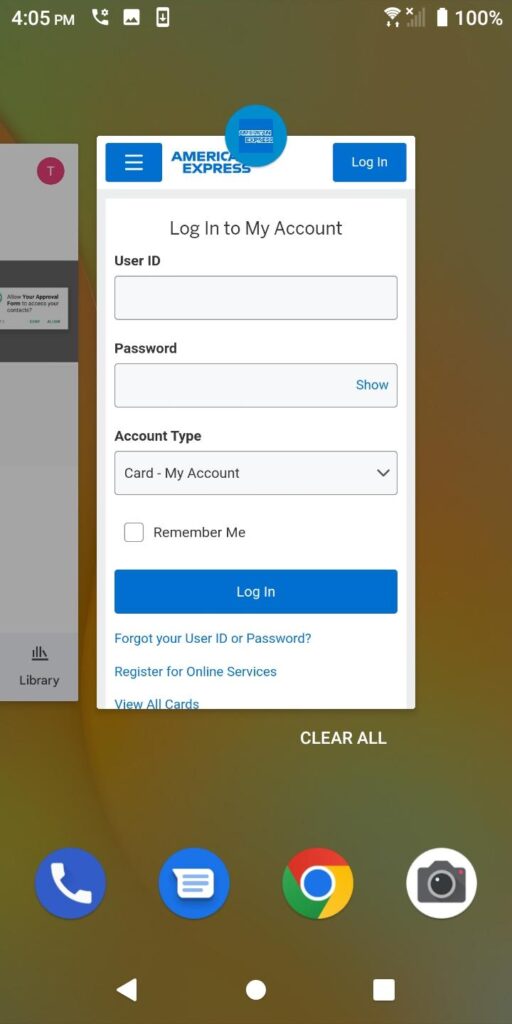
The app then loads the real American Express login page in a custom inline browser where it presents the User ID and Password fields for your AMEX account.
It looks very legitimate, but because of the inline browser, it’s actually a potent phishing tool to scrape and steal your information.
 |
 |
With the malicious application now able to steal your login credentials from the inline browser, any information you enter into this login will be transmitted to the threat actors.
Worst of all, any multi-factor authentication code normally sent to you via SMS will also be intercepted by the application as it’s now set as the device’s default messaging app as well.
In fact, you won’t even see the SMS verification code because – surprise – this isn’t a messaging app!
Malicious URL Detection
While this malicious campaign’s multi-step takeover process may seem laborious on paper, in reality it is quite low-effort to detonate. Therefore, it will probably see some level of success in the real world.
It’s definitely a bizarre campaign, but unfortunately, that doesn’t mean it won’t be effective.
Naturally, it goes without saying that malicious URLs should be stopped way upstream of this interaction.
A secure email gateway, secure web gateway, or even DNS provider with the latest threat intelligence would have caught this and sanitized or blocked the URL.
alphaMountain is a leading provider of URL threat intelligence, often detecting malicious links days before any other source.
In fact, as of this writing, we are the only threat intelligence source that’s identified this URL as malicious on VirusTotal, some three days after the domain’s registration. See below.
To see how alphaMountain can improve the threat detection of your security product, platform or program, request your free trial API key and try it out for yourself.