Cybercrime is getting more complex. Threat actors are no longer satisfied with just one bite at the proverbial apple. Remember the good old days when a DDoS attack could be shut off for a small crypto payment? Those days are over.
Today, cybercriminals are embedding multiple malicious activities behind single points of entry in their campaigns. This means that they are combining threats like phishing with malware delivery and unleashing them on underprotected and apathetic citizens at scale.
To succeed in these campaigns (whether it’s for credentials, payment information, or any other thing of value), threat actors are relying more and more on brand impersonations of the companies that people know and love. The reason is obvious. If a threat actor can legitimize the appearance of their campaigns, the more likely they are to succeed.
In this post we’re tearing down a recent multi-threat email campaign purported to be from the Helpful Hardware Company, better known as ‘ACE’.
It starts with an email telling the user they have won a reward from a trusted retailer. This was an important strategic decision by the threat actors. ACE is a brand that’s ubiquitous enough to land in enough inboxes where recipients are actual ACE customers. This probability of association leads to higher success rates.
ACE Is NOT the Place
Notably, the choice of creative elements is important here, too. The prize offered is the type one would logically find at an ACE hardware store, but certain issues stick out as suspicious right away. The inconsistent capitalization in the call to action and the lack of branding on the mention of Cuisinart stand out as Cuisinart is another well-known brand from whom legitimate ACE marketing professionals would have had very strict co-brandings requirements for a promotion like this.
In any case, driven by FOMO (that’s ‘fear of missing out’ if you didn’t already know), most consumers won’t spot these red flags and will click on through. So, let’s explore what happens then.
Post-Click Technical Analysis
The initial call to action link is hosted on a subdomain of googleapis[.]com as a sneaky way to get through URL filtering:
https://cio_mailpro_bulkmail-2024___________w87x5230_8940152.storage[.]googleapis[.]com/CCCWWWSSDFNNNTTTGGGRRLL____________________HHRRDDWWRRAACCC___1-1……..HTM
It returns an HTML page with:
<meta http-equiv=”refresh”content=”0; url=https://bundlesnaper.com/0/0/0/a673a6269436e5c9134654dda2da172c”>
When we follow…
https://bundlesnaper[.]com/0/0/0/a673a6269436e5c9134654dda2da172c
…it returns a page with:
<script type=”text/javascript”>window.location.href=”https://inhalehold.click/?s1=351648&s2=1071659555&s3=5798&s4=3074&s10=3138″</script>
When we follow…
https://inhalehold.click/?s1=351648&s2=1071659555&s3=5798&s4=3074&s10=3138
…it returns a page with:
<script>window.history.pushState({},””, “/14888c449092bcfa9196bbab991de227”);function _0x4eba(_0x4c03d2,_0xe4b087){const _0x3ccf2d=_0x3ccf();return _0x4eba=function(_0x4eba2c,_0x13dff7){_0x4eba2c=_0x4eba2c-0x14f;let _0x22a516=_0x3ccf2d[_0x4eba2c];return _0x22a516;},_0x4eba(_0x4c03d2,_0xe4b087);}(function(_0x5868e6,_0xfff814){const _0x61528b=_0x4eba,_0x48fdb1=_0x5868e6();while(!![]){try{const _0xbf18a1=-parseInt(_0x61528b(0x157))/0x1+-parseInt(_0x61528b(0x161))/0x2*(-parseInt(_0x61528b(0x15b))/0x3)+parseInt(_0x61528b(0x158))/0x4+parseInt(_0x61528b(0x159))/0x5*(-parseInt(_0x61528b(0x150))/0x6)+parseInt(_0x61528b(0x162))/0x7*(-parseInt(_0x61528b(0x14f))/0x8)+-parseInt(_0x61528b(0x160))/0x9+parseInt(_0x61528b(0x15a))/0xa*(parseInt(_0x61528b(0x152))/0xb);if(_0xbf18a1===_0xfff814)break;else _0x48fdb1[‘push’](_0x48fdb1[‘shift’]());}catch(_0x1e48ac){_0x48fdb1[‘push’](_0x48fdb1[‘shift’]());}}}(_0x3ccf,0xd0dc4),((()=>{let _0x1d24a4;function _0x317ee9(){const _0x34cb72=_0x4eba;_0x1d24a4=new XMLHttpRequest();if(!_0x1d24a4)return![];_0x1d24a4[_0x34cb72(0x156)]=_0x14768a,_0x1d24a4[_0x34cb72(0x15e)](_0x34cb72(0x151),’?_ax=w’),_0x1d24a4[_0x34cb72(0x154)](),console[_0x34cb72(0x15f)](_0x1d24a4[_0x34cb72(0x15d)]);}_0x317ee9();function _0x14768a(){const _0x3e6157=_0x4eba;_0x1d24a4[_0x3e6157(0x155)]===XMLHttpRequest[‘DONE’]&&(_0x1d24a4[‘status’]===0xc8?document[_0x3e6157(0x153)](_0x1d24a4[‘responseText’]):document[‘write’](_0x3e6157(0x15c)));}})()));function _0x3ccf(){const _0x4e0fa3=[’20iBklxX’,’3RUyOcx’,’404\x20Not\x20Found’,’status’,’open’,’log’,’4644783xMERJb’,’1603608HBMLux’,’851711lCRkkF’,’8NjYPVK’,’54906ougbtT’,’GET’,’9024521mDxWGt’,’write’,’send’,’readyState’,’onreadystatechange’,’1107944AVyirZ’,’853904xkZFwm’,’30rgSiNk’];_0x3ccf=function(){return _0x4e0fa3;};return _0x3ccf();}</script>
That function eventually deobfuscates to this:
window.history.pushState({}, “”, “/14888c449092bcfa9196bbab991de227”);
function initializeXHR() {
let xhr;
function handleResponse() {
if (xhr.readyState === XMLHttpRequest.DONE) {
if (xhr.status === 200) {
document.write(xhr.responseText);
} else {
document.write(“404 Not Found”);
}
}
}
xhr = new XMLHttpRequest();
if (!xhr) return false;
xhr.onreadystatechange = handleResponse;
xhr.open(“GET”, “?_ax=w”);
xhr.send();
console.log(xhr.readyState);
}
initializeXHR();
This initiates a background request to this URL…
https://inhalehold.click/14888c449092bcfa9196bbab991de227?_ax=w
…which renders this page:
Technical Process Tree Translation
Let’s translate a lot of this web activity into a sequence that’s a little easier to understand by humans. From the email click to the rendered page, the adversary used the following evasion techniques:
- Link to an “benign” page on a “trusted” domain (googleapis.com)
- Host phish page on a site registered that same day
- HTML “redirect” (http-equiv refresh)
- Javascript “redirect” (window.location)
- Obfuscated javascript
- Background request to load page content (XHR)
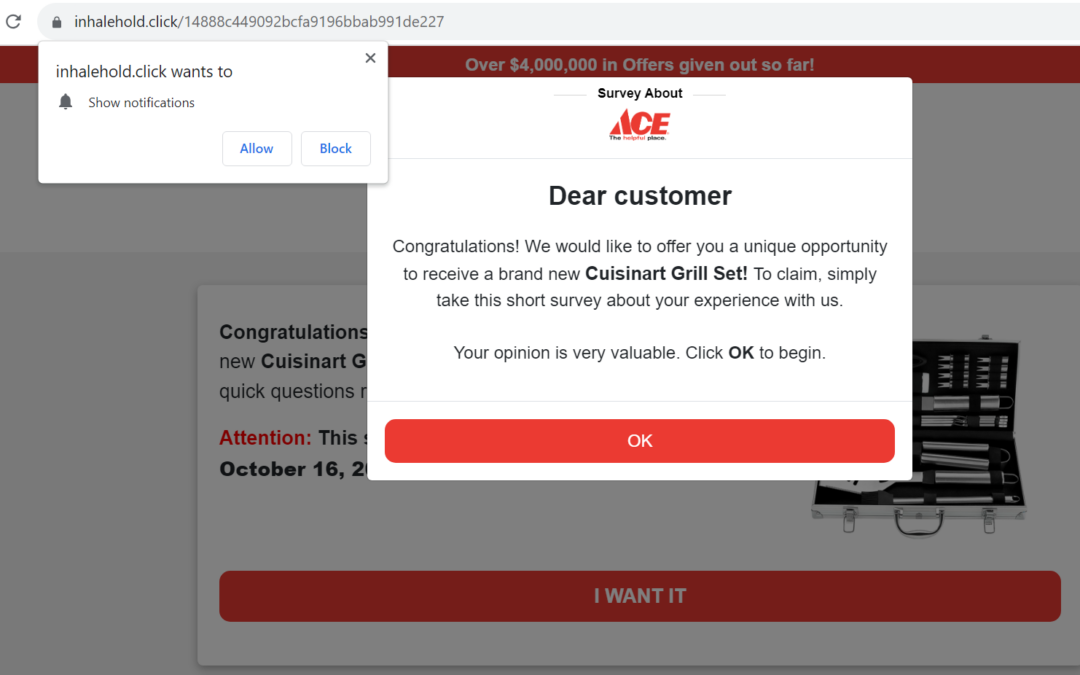
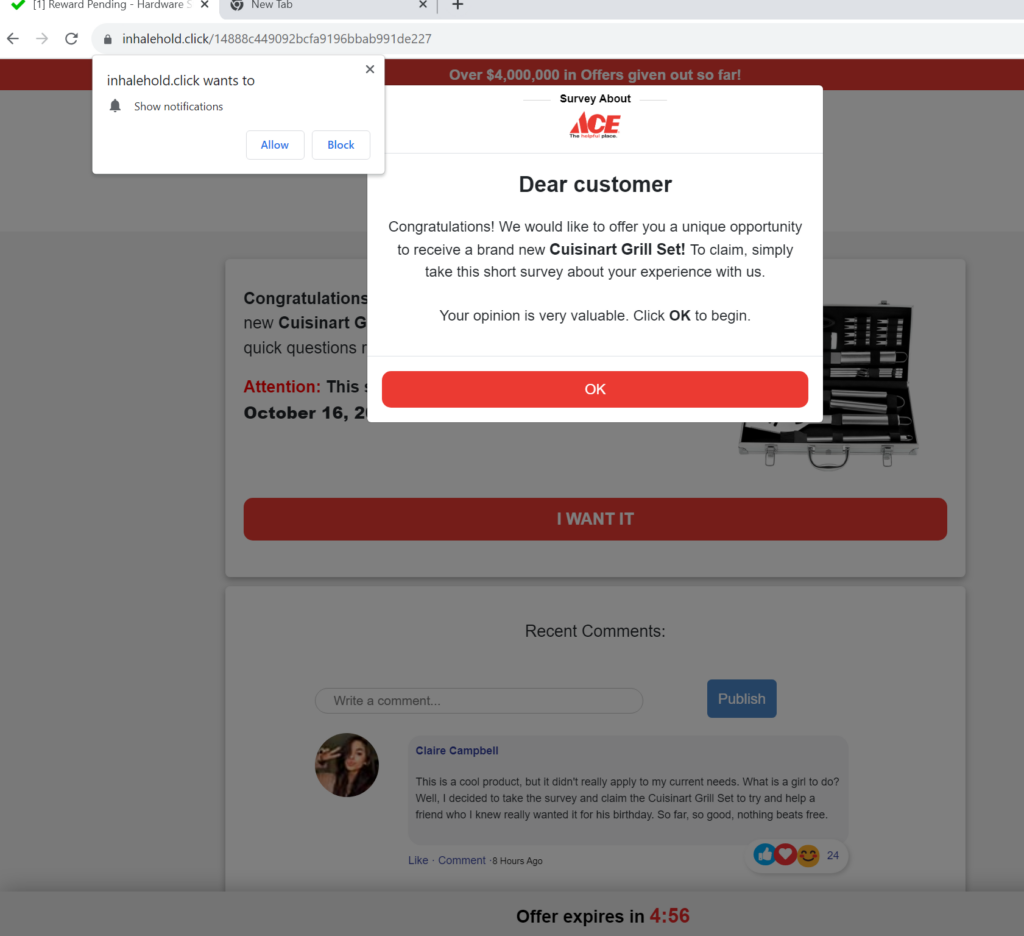
The initial page has two pop ups:
- The browser asks if it can send notifications for this site.
- Confirmation that you want to start the survey to claim your prize
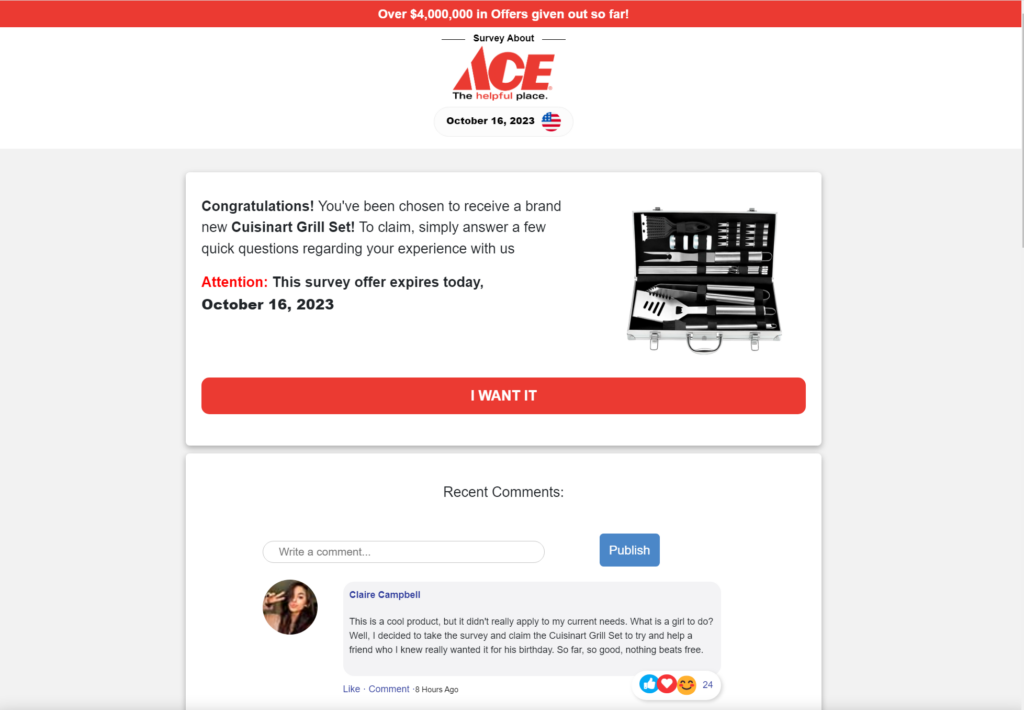
After clearing the pop ups, the page looks like this:
Most of what just happened in the background would likely go unnoticed by a deal-seeking consumer. At this stage, if the landing page isn’t visually compelling, most users would begin to doubt its authenticity, so it makes sense that the threat actors have invested here to make it trustworthy. Notice a few things about this landing page:
- Convincing ACE branding
- Just take a short survey to get your reward
- Timed offer, with current date and countdown clock
- Compelling-but-fake reviews (with likes!)
- “Over $4,000,000 in Offers given out so far!”
- Offer expires the same day
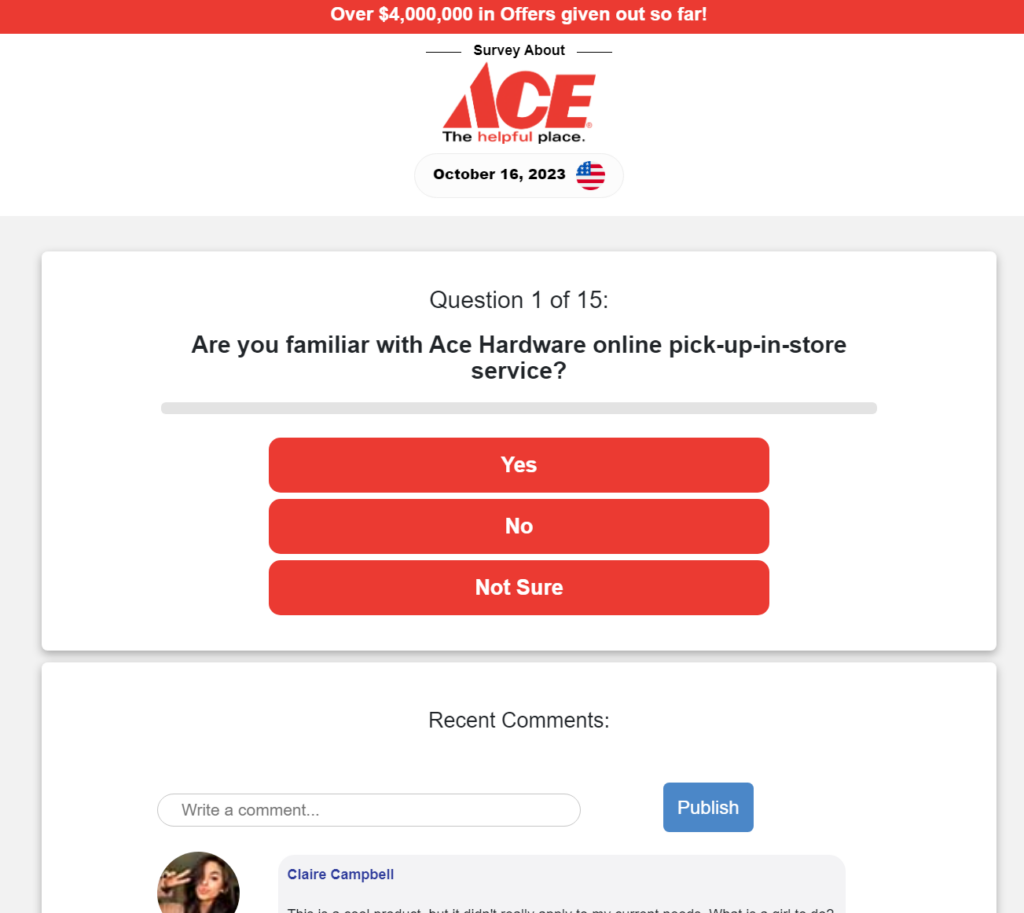
Once you click “I WANT IT” (of course, who doesn’t at this point?), the survey takes you through 15 easy questions.
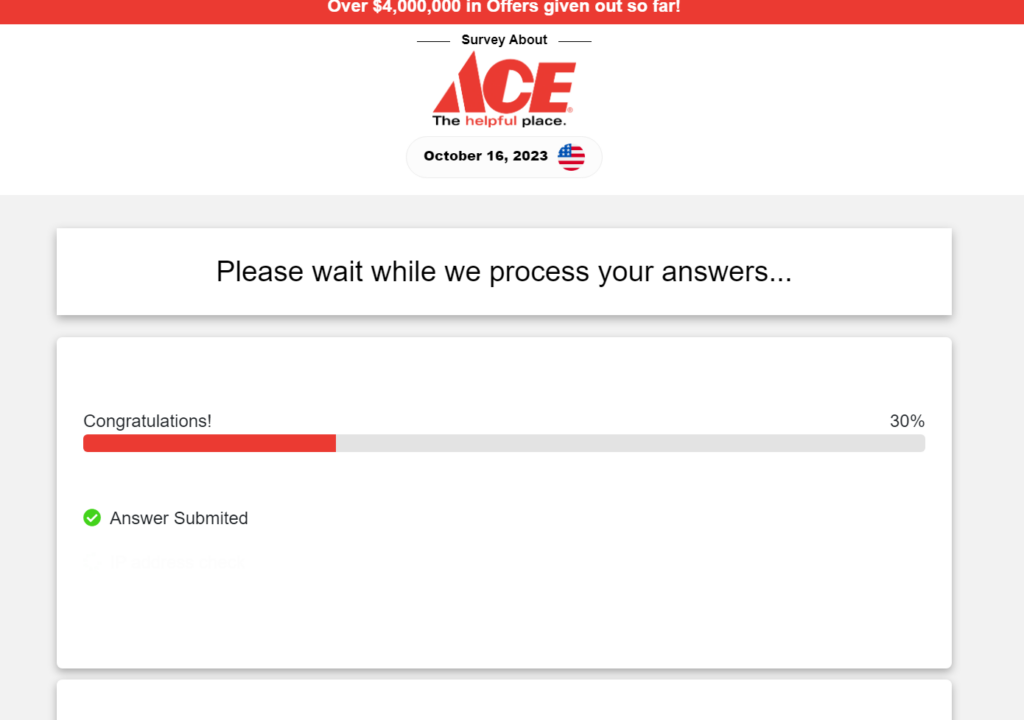
After the survey is complete, it says “processing answers…” for a minute and then says the reward can be claimed.
Following the “acceptance” of your survey answers, the system then presents you with a prize selection.
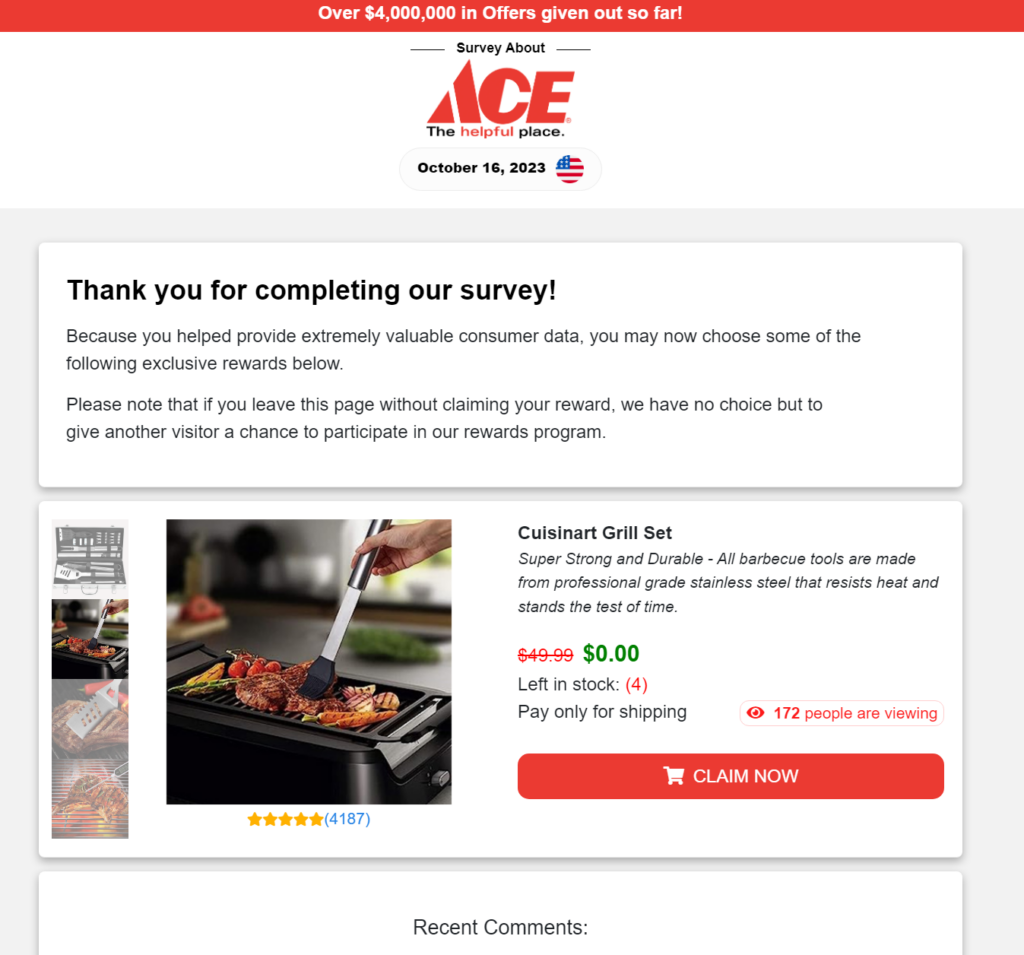
Remember Pop Ups?
There are three really compelling pieces of information on this claims page. The first is the crossed out retail price showing $0.00 in green. This is the value anchor that validates the user’s investment of time. The second is the stock indicator showing just (4) units left in stock, and the third is the view counter indicating that 172 people are currently viewing this offer. This combination of dual urgency triggers is brutally-effective at getting users to complete the next step by clicking the ‘CLAIM NOW’ button.
Speaking of investment, it’s also worth noting that the threat actor’s decision to include such a substantial and well-designed survey was very savvy. By forcing the user to invest a significant amount of time in completing the survey, the likelihood increases that they will see it to its completion. With “skin in the game” now, users are almost certain to seek some return on their investment. This is another smart move by the threat actor towards perpetrating this crime.
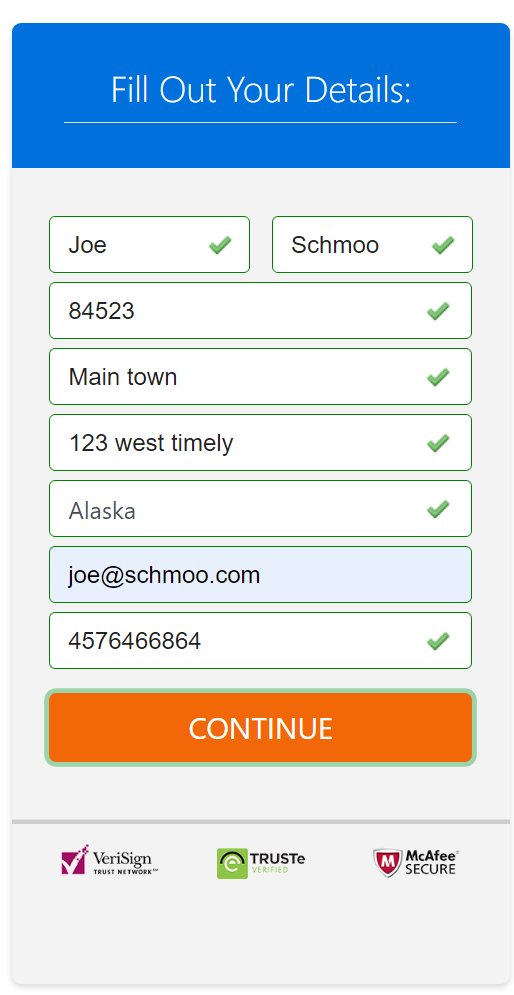
After agreeing to continue, it sends you to another “verified safe” site to fill out your shipping and credit card information:
https://www[.]cyberselectivedeals[.]com/heavy-duty-bbq-grill-tool-set-in-case/51331936/?affid=[…]uXYXcVPvb&c3=&click_id=7dfbbb45ab914794bca7ccf6128025c6
The reason they send you to another site is because the actual phish site (where they take CC) will likely get picked up as malicious before the survey site, so the perpetrators rotate where they send you to take your credit card without compromising the integrity of the survey site. Again, this is smart and sneaky.
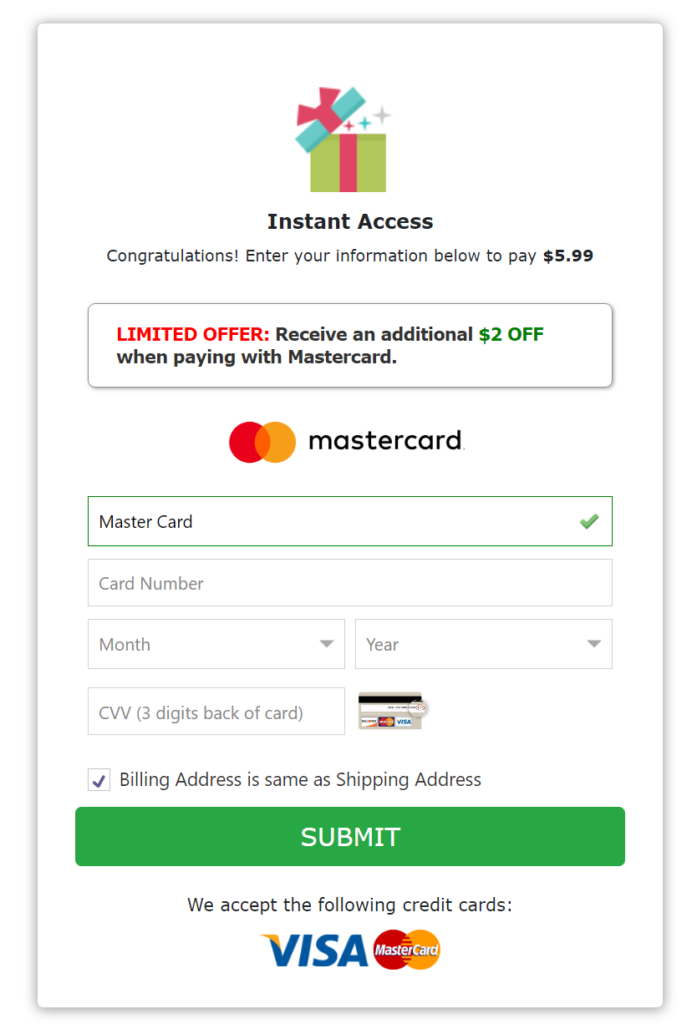
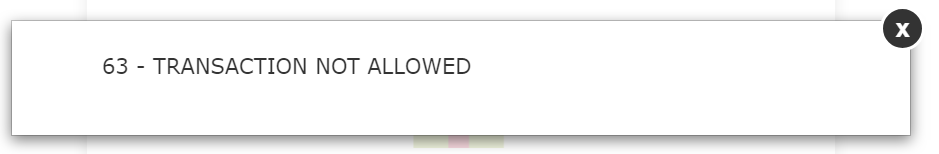
The form Includes some validation of inputs, but not much, as it accepts some random address info. It does appear to validate credit cards, as a fake one comes back with an error.
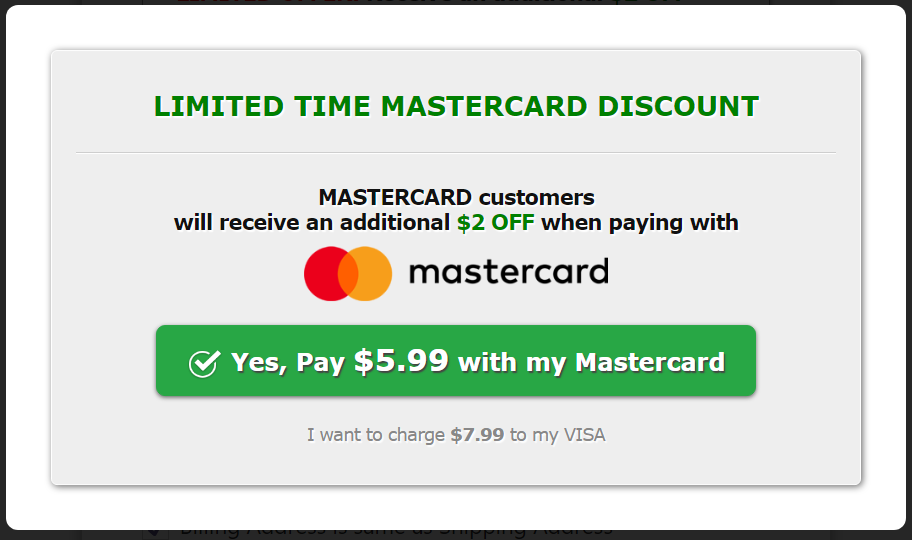
Apparently, for reasons unclear, the adversaries prefer MasterCard over VISA, so they offer a discount. Putting a VISA card number in, it pops up and asks for MasterCard on every number entered.
In any case, with this information submitted, the threat actors have successfully completed the first mission in their multi-threat campaign and they will be able to monetize either the use or resale of your credit card information.
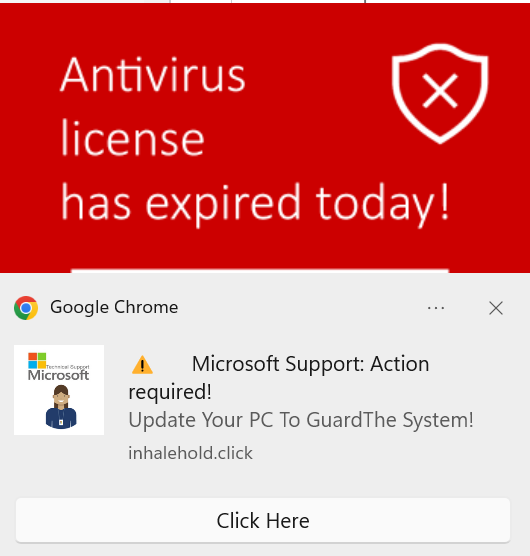
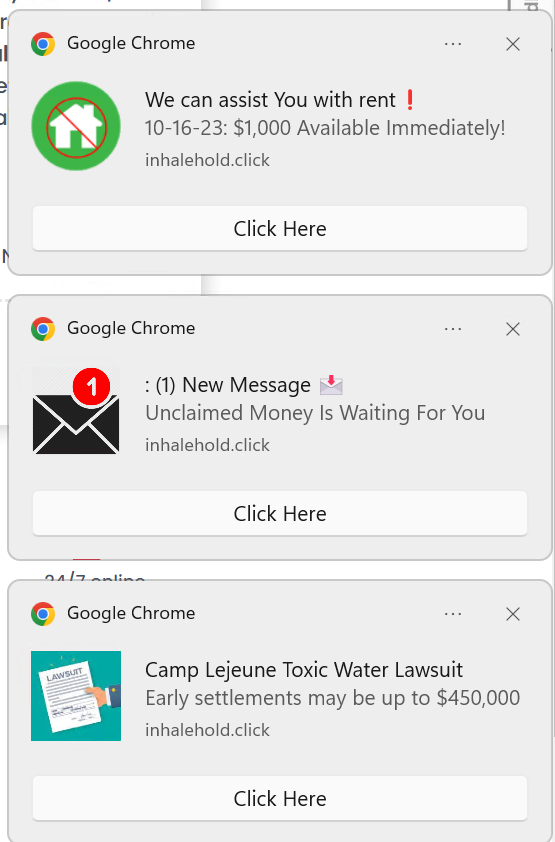
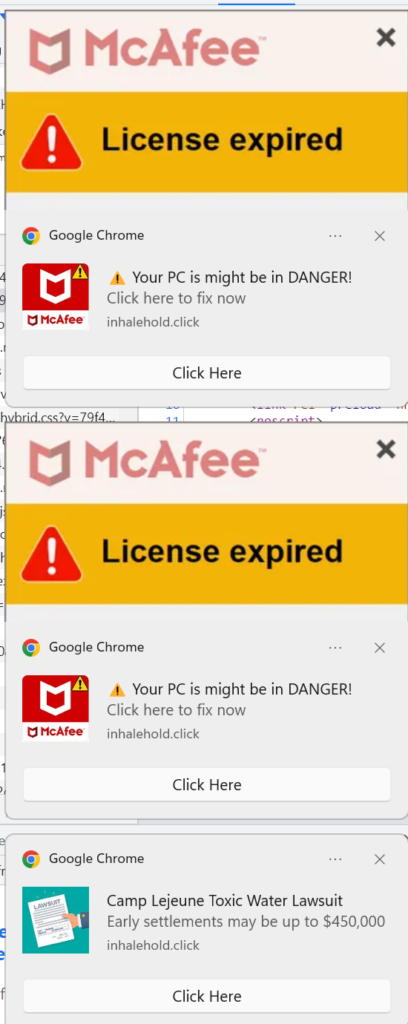
Now, back to the browser popup request. A site can request to send notifications to the user. There are all sorts of legitimate and benign reasons for this, including for an application like Google calendar, to remind you of upcoming appointments. Unfortunately, that’s not what’s happening here. After agreeing to allow this site to notify the user, you start to get ads like these:
Thus begins the second part of this three-part campaign. After you are done getting scammed by the survey and reward phish, you get bombarded with an incessant stream of ads for other scams.
Of note, the McAfee AV ads does actually send you to McAfee’s real website to buy the product. They do redirect through several intermediate servers first, but ultimately you end up at the real McAfee website to purchase the product. They pass in an affiliate code to the website, presumably get some royalty on the coerced sale of antivirus to the exasperated victim.
Every time you close one of the popup ads, window tabs open and more ads appear. It never ends.
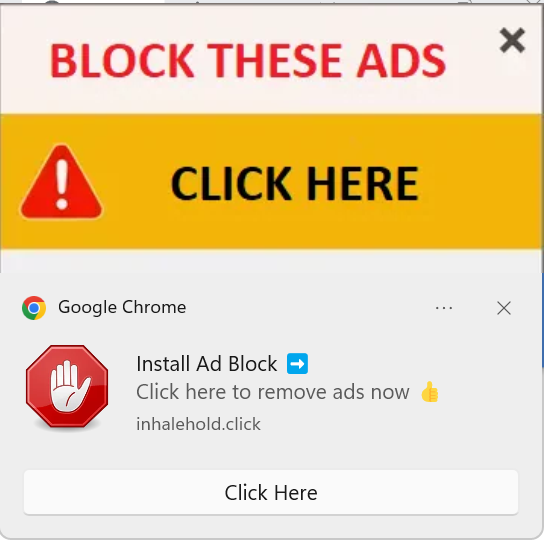
Finally, if you manage to close all the antivirus popup ads (either through fast reflexes or ecommerce extortion), one appears with this offer:
This is an offer for you to install a malicious Chrome Extension to block these ads. We didn’t click on that, but installing this extension would mark the successful conclusion of this third part of the three-part campaign by the threat actors. Would it end there? Unlikely.
Who said cybersecurity isn’t fun?
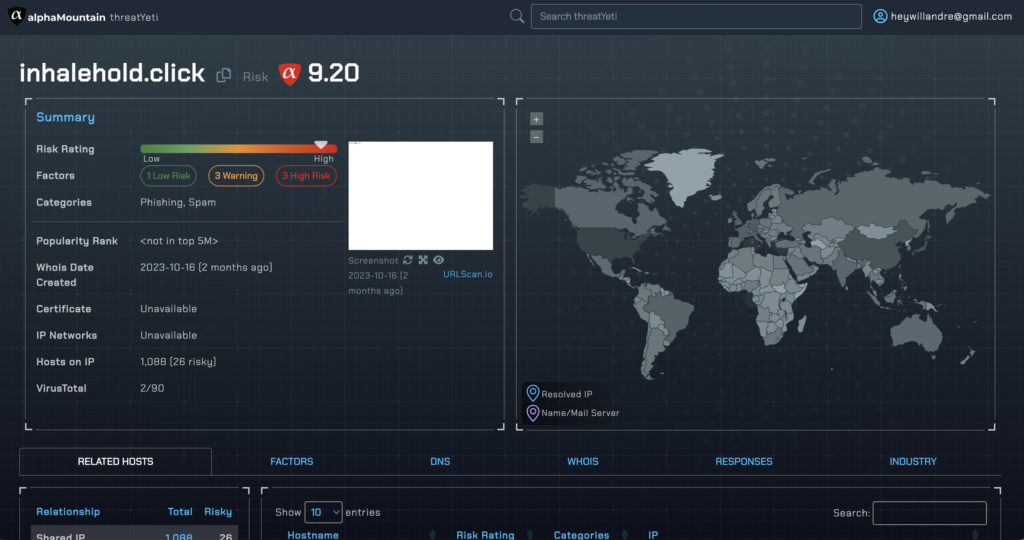
Speaking of fun, let’s run the URL from that Chrome extension into threatYeti, alphaMountain’s domain and IP threat search engine.
As expected, it’s no place you want to be.